Newly Registered Domain names – a threat to corporate and consumer security posture
By Gareth Jehu, Global Operations Director
Domain names are mission critical brand assets and consumers trust them to signpost to authentic content and services. Disruption to domain name and DNS services means our email stops working, apps and websites cannot be readily found or the confidentiality, integrity and availability of corporate and consumer data is compromised.
Newly Registered Domain Names common in cybercrime
Both academic and industry research is suggesting that this trust in domain names is being undermined by threat actors who are using Newly Registered Domain Names (NRDs) to engage in cybercrime activities such as phishing campaigns and malware distribution.
In a recent study which looked at registration activity across 1530 top level domains, UNIT 42, the global threat intelligence team at Palo Alto Networks® concluded that more than 70% of NRDs (those domains registered in the last 32 days) are potentially “malicious”, “suspicious” or “not safe for work.”
Which domain registries are targeted?
Unsurprisingly, .com still accounts for the lion’s share of NRDs. However UNIT 42’s research found that .com NRDs are more likely to be associated with legitimate, trustworthy services and content whilst it is in the ccTLD namespace that we find the highest ratio of malicious NRDs. This is largely attributed to the relatively low barriers to acquisition that include inexpensive or free registration, relaxed registration policies and redacted WHOIS. The graph below (taken from UNIT 42’s research) highlights the top 15 TLDs with the highest malicious NRD rate.
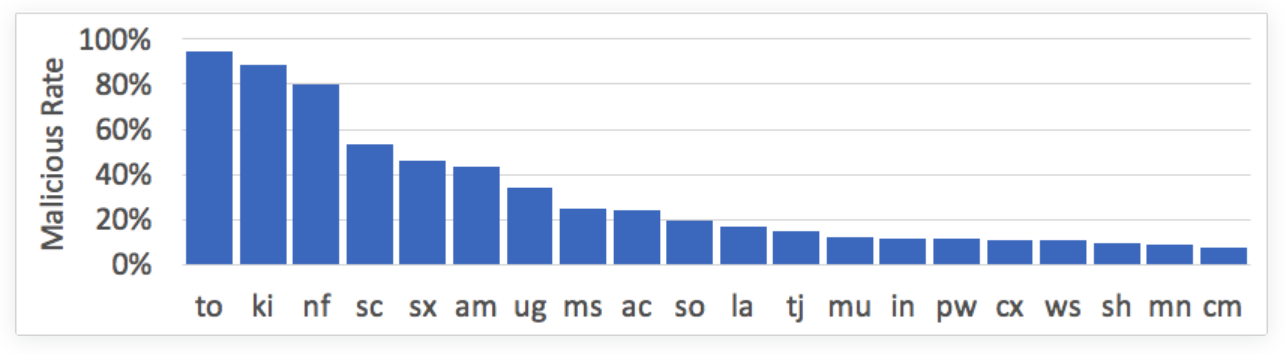
These trends are indeed a cause for concern and executives, managers and administrators involved in Information Security and improving corporate security posture should consider implementing appropriate controls to mitigate against the risk of falling foul to NRD nefarious activities. This is easier said than done, as many of these domain names are only kept alive for a matter of hours or days which makes it difficult to even be aware that a threat exists.
Steps you can take to protect yourself
Palo Alto Networks recommend blocking access to either all NRDs or to those TLDs that are exhibiting the highest rates of malicious activity. Whilst blocking is a high strength mitigation control, it does carry the risk of creating false positives and blocking legitimate traffic. As an alternative, administrators might consider traffic monitoring for an early warning to potential malicious activities originating from NRDs.
In the end, it is all about your organisations risk appetite. What is the price of the maintenance of client trust?
